In Oracle RAC environment , if you face the below error:
ORA-46362: Could not translate variable ORACLE_BASE
*** Solution:
Modify the database resource:
srvctl setenv database -db [DBNAME] -env ORACLE_BASE=$ORACLE_BASE
In Oracle RAC environment , if you face the below error:
ORA-46362: Could not translate variable ORACLE_BASE
*** Solution:
Modify the database resource:
srvctl setenv database -db [DBNAME] -env ORACLE_BASE=$ORACLE_BASE
One of the new exciting new security features in Oracle 12cR2 (12.2.0.1) , is the ability to encrypt your tablespaces “online“. In the past Implementing TDE required creating a new encrypted tablespace and then moving the data from the original tablespace to the encrypted tablespace (export/import data pump operations), which means a down time of your systems unless you use active data guard which minimizes TDE conversion implementation.
Let us now explore and simulate:
Current environment is: Oracle 12cR2 (Container Database Architecture) in Windows OS
Current ORACLE_HOME=C:\app\emodb\product\12.2.0\dbhome_2
Create a directory for the key store:
C:\app\emodb\product\12.2.0\dbhome_2\key_store
Go to sqlnet.ora file and add the below lines:
ENCRYPTION_WALLET_LOCATION=
(SOURCE=
(METHOD=file)
(METHOD_DATA=
(DIRECTORY=C:\app\emodb\product\12.2.0\dbhome_2\key_store)))
SQL> ALTER SYSTEM SET COMPATIBLE = ‘12.2.0.0’ SCOPE = SPFILE;
Then execute:
SQL> ADMINISTER KEY MANAGEMENT CREATE KEYSTORE ‘C:\app\emodb\product\12.2.0\dbhome_2\key_store’ IDENTIFIED BY super_mario$88;

ewallet will be created:
Open the key store by executing:
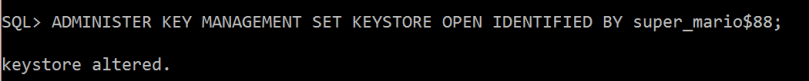
SQL> ADMINISTER KEY MANAGEMENT SET KEYSTORE OPEN IDENTIFIED BY super_mario$88;
Now I will create the Master Key:
SQL> ADMINISTER KEY MANAGEMENT SET ENCRYPTION KEY IDENTIFIED BY super_mario$88 WITH BACKUP USING ‘mario_bck7’;

Backup of key store generated (it’s better to place it in a different directory)
I have already created and activated a master key in the root container and, one in each of the pluggable databases. Now I will create local master key for pluggable database
SQL>alter session set container=PDBORCL;
SQL>ADMINISTER KEY MANAGEMENT SET KEYSTORE OPEN IDENTIFIED BY super_mario$88;
SQL>ADMINISTER KEY MANAGEMENT SET KEY IDENTIFIED BY super_mario$88 WITH BACKUP;
Now the interesting part…..the online tablespace conversion:
I will run the alter tablespace command to encrypt an existing tablespace named “COMPANY_INFO_TS”:
SQL>ALTER TABLESPACE COMPANY_INFO_TS ENCRYPTION ONLINE USING ‘AES256’ ENCRYPT FILE_NAME_CONVERT = (‘COMPANY_INFO.DBF’, ‘COMPANY_INFO_ENC.DBF’);
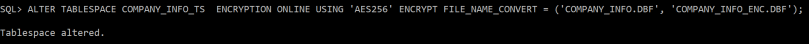
If you don’t specify the encryption algorithm, the default encryption will be AES128
Encrypted new data file is generated:
of course you need to increase the tablespace size before your start the conversion, as the conversion process will require more space allocation.
You can use DataWalker for Oracle to test viewing the data file blocks that is not encrypted, and encrypted one:
http://www.toolswatch.org/2014/03/new-tool-datawalker-for-oracle-v1-0-in-the-wild/
Useful queries:
** to check wallet status
SELECT * FROM v$encryption_wallet;
** to check encryption keys created 1 in CDB and the other in PDB database:
SELECT con_id, key_id FROM v$encryption_keys;